Microsoft Defender ATP is GA since June 28, 2019 and no clear tutorial or implementation guide has been written before! I hope this clarify the simplicity of this implementation!
- Intune App Wrapping Tool Macos X
- Intune App Wrapping Tool Macos Update
- Intune App Wrapping Tool For Macos
- Intune App Wrapping Tool Macos Operating System
- Intune App Wrapping Tool Macos 7
This post assumes that you perform the tasks and file preparation on a macOS machine. Preparing the onboarding package and files. Access the Microsoft Defender Security Center and gather the installation and onboarding package: To deploy the installation package with Microsoft Intune we need the Intune app wrapping tool for macOS which is. Note: ' Use the Microsoft Intune App Wrapping Tool for macOS to pre-process macOS line-of-business apps. The wrapping tool converts application installation files into the.intunemac format. The wrapping tool also detects the parameters required by the mobile device management (MDM) agent to determine the application installation state. Jul 23, 2018 Normally we would do this by wrapping the Graph API calls (REST) into some PowerShell functions and build the logic for the described process. Luckily Microsoft released a new PowerShell Module WindowsAutoPilotIntune (thx to @mniehaus) based on the Graph API to import new AutoPilot information into Intune.
- Are you ready for the next-generation protection in the road to Security Operations?
- Are you willing to act on insights on your MAC OS X machines?
Download installation and onboarding packages!
- Download the installation package from: https://securitycenter.windows.com/
- Download the onboarding package from: https://securitycenter.windows.com/
Microsoft Intune App Wrapping Tool for macOS
- Download the IntuneAppUtil from: https://docs.microsoft.com/intune/lob-apps-macos
- Open a terminal, navigate to your download folder and make IntuneAppUtil executable with: Chmod +x IntuneAppUtil
- Now generate the intune deployment package with: ./IntuneAppUtil -c wdav.pkg -o . -i “com.microsoft.wdav”
- Unzip the windowsDefenderATPOnboardingPackage
Login to your devicemanagement portal
- Login to devicemanagement.microsoft.com
- Navigate to Microsoft Intune / Microsoft EndPoint manager
Add the kernel extention file: (more info)
- In Intune, open Manage > Device configuration. Select Manage > Profiles > Create Profile.
- Enter a name, description, Platform = MACOS, Profile Type Custom
- Choose a custom configuration profile name: mdatp-kext
- Upload the kext.xml from the intune folder.
- Click OK
- apply this policy on all MAC devices. (or the one you want to apply)
Now add the actual onboarding file with the same procedure as the previous one
- Repeat the procedure above but now with WindowsDefenderATPOnboarding.xml
Deploy the Line-of-business app for OSX
Intune App Wrapping Tool Macos X
- Go to your Client Apps - add line of business app
- Add the earlier createdwdav.pkg.intunemac
- Define the name, description, publisher & minimum operation system
- When your upload is completed, select the assignment and assign your pacakge to you Mac collection!
- Run a detection test from a terminal session: curl -o ~/Downloads/eicar.com.txt http://www.eicar.org/download/eicar.com.txt
- Wait for the test to see the results!
Bring it all together!
- Microsoft Defender is cross-platform and offers a next-generation protection and endpoint detection for MAC!
- Because of the intelligence organizations will be able to have a better insight of the usage & risks of their MAC environment.
- Also check the official demo of Microsoft Defender for MAC.
- Let's built the next generation SEC OPS!
- Microsoft is leading in 2019 Endpoint Protection Platforms Magic Quadrant!
Also see
Published By
Jasper Bernaers
Chief Technology Officer at Synergics | MC2MC
Microsoft Defender ATP (MDATP) for macOS hit finally the public preview status. We can now protect our macOS endpoints with cloud based power. I created a little guide about the onboarding process with Microsoft Intune and the user experience.
Intune App Wrapping Tool Macos Update
Prerequisites
From a macOS endpoint perspective:
- macOS version 10.12 (Sierra) or newer
- No third party endpoint protection installed
- At least 1GB of free disk space
- macOS client enrolled in your Intune tenant
Intune App Wrapping Tool For Macos
If you want to enable macOS enrollment for your Intune tenant - I’ve written a post about the enrollment process.
From a Microsoft 365 perspective:
- Microsoft Defender ATP license (Windows 10 Enterprise E5)
- Intune tenant wit macOS enrollment enabled
- Access to the Microsoft Defender Security Center
- Appropriate user rights to create and assign an Intune device configuration, LOB App
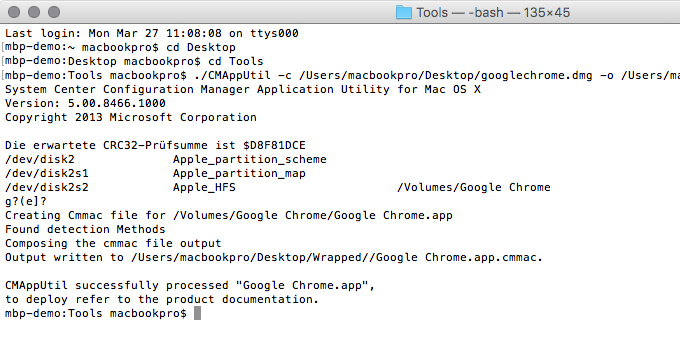
This post assumes that you perform the tasks and file preparation on a macOS machine.
Preparing the onboarding package and files
Access the Microsoft Defender Security Center and gather the installation and onboarding package:
To deploy the installation package with Microsoft Intune we need the Intune app wrapping tool for macOS which is available here.
Now you should have these three files:
Open a terminal and perform the following actions:
Make the IntuneAppUtil executable:
chmod +x IntuneAppUtilGenerate the Intune deployment package:
./IntuneAppUtil -c wdav.pkg -o . -i 'com.microsoft.wdav'Unzip the onboarding package:
unzip WindowsDefenderATPOnboardingPackage.zipwe’ll need the files in the unzipped intune folder later
When you have successfully completed the above steps, the file structure looks like this:

Intune portal configuration
In the Intune portal create a custom device configuration to deploy the Microsoft Defender ATP kext.xml (kernel extension). Upload the kext file from the previously extracted zip file which is located in the Intune folder. These kernel extensions will be loaded into the macOS operating system on boot for the Microsoft Defender ATP service.

For the actual onboarding of the macOS machine to your MDATP tenant we need the onboarding configuration “WindowsDefenderATPOnboarding.xml” which contains encrypted tenant info. You find the file also in the unzipped package in the Intune folder. To deploy this file create another custom device configuration and upload the xml file:
To deploy the Microsoft Defender ATP package create a new LOB (Line-of-business-app) and upload the wrapped *.intunemac file:
Provide the required app information and make sure to set the minimum operation system version to Sierra as mentioned in the prerequisites:
Furthermore make sure that you assign both device configurations and the LOB app to your targeted Azure AD group.
Resultant macOS experience
Intune App Wrapping Tool Macos Operating System
After the device configurations were applied a new icon pops up on your macOS device:
And here’s a snippet of the main app:
Intune App Wrapping Tool Macos 7
To end this post here’s the machine view from the MDATP security dashboard:
Reference: